Dynamic Data Masking
What is Dynamic Data Masking?
Dynamic Data Masking is a masking approach designed to obscure sensitive information in real-time, ensuring that only authorized users can access and view the complete data. Unlike static data masking, which applies a uniform mask to all users, dynamic masking tailors the level of data exposure according to the user’s role or permissions.
In layman’s language, it dynamically alters data visibility based on user roles or access privileges, while unauthorized or lower-privileged users perceive a masked or redacted version of the information. It ensures a granular and customizable security layer by intercepting database queries and applying masking rules, significantly preventing data breaches, internal threats, and non-compliance issues.
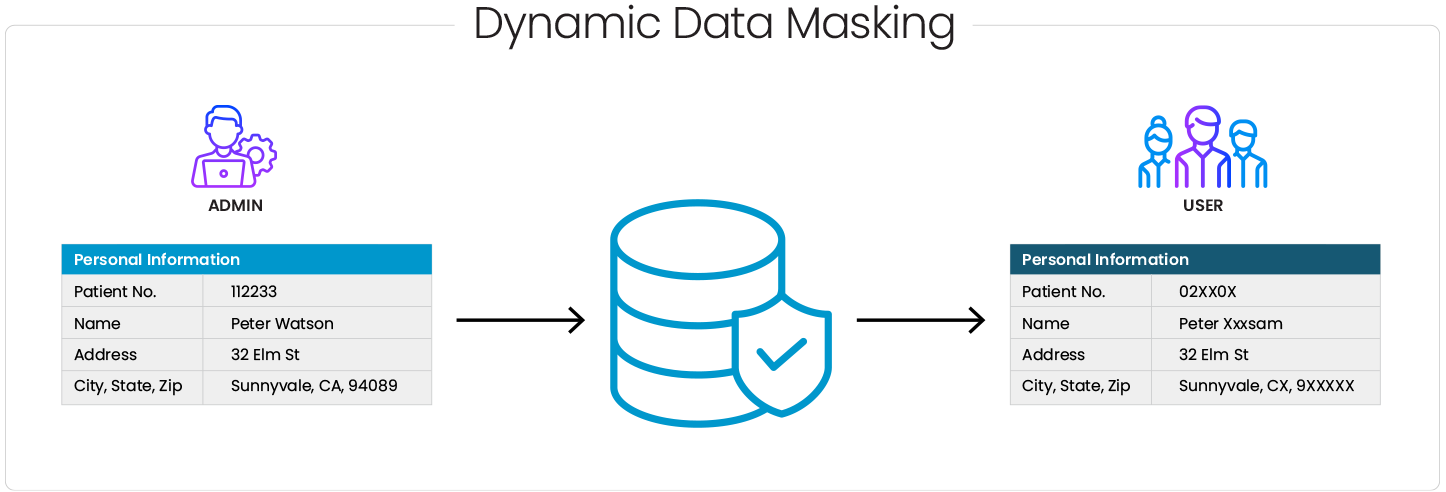
Pictorial representation of how Dynamic Data Masking Works?
How Dynamic Data Masking Works?
The fundamental principle behind DDM lies in its ability to intercept and modify database queries on the fly, dynamically adjusting the visibility of specific data elements based on user permissions.
- Masking Rules: Dynamic masking relies on predefined rules to control how sensitive information is shown to different users or roles. These rules are crafted to align with security policies and compliance requirements.
- Policy Enforcement: Dynamic masking enforces different masking rules at the database level, acting as a gatekeeper to sensitive information. The policies are consistently applied, ensuring a seamless and secure experience for users interacting with the database.
- Role-Based Access Control (RBAC): Integration with RBAC mechanisms allows dynamic masking to synchronize with the organization’s user roles. This alignment ensures that data exposure is customized based on users’ specific roles and responsibilities, providing a fine-tuned approach to data security.
- Real-Time Adaptability: One of the key features of dynamic masking is its dynamic nature. As user permissions change or new security policies are implemented, the masking of sensitive data adapts in real time. This adaptability ensures that the data security measures remain effective in evolving user access scenarios.
Dynamic masking combines these elements and offers a granular and customizable security layer. Its real-time, adaptive approach significantly enhances data security, making it crucial in safeguarding against unauthorized access and potential data breaches.
Difference between Static and Dynamic Data Masking:
Unlike dynamic data masking, static masking involves a one-time transformation, making it especially well-suited for scenarios where constant protection is imperative. The primary goal is to create a structurally similar yet fictitious version of the original data, ensuring that sensitive elements remain concealed while maintaining the overall integrity and usability of the dataset.
| Feature | SDM | DDM | On-the-Fly Masking |
|---|---|---|---|
| Timing | Before data storage | During data access (real-time) | During data access (real-time) |
| Masking Rules | Pre-defined | Based on user permissions | Based on specific situations |
| Data Type | More efficient for structured data | Efficient for structured and unstructured data | Efficient for structured and unstructured data |
| Advantages | Simple, Efficient | Granular control, Real-time access | Real-time, Context-aware |
| Disadvantages | Not real-time, Inflexible | More complex, Performance impact | More complex, Performance impact |
Adaptability of Masking Techniques Across SDM and DDM:
| Technique | SDM | DDM | On-the-Fly Masking |
|---|---|---|---|
| Shuffling | Yes | Yes | Yes |
| Redaction | Yes | Yes | Yes |
| Tokenization | Yes | Yes | Yes |
| FPE | Yes | Can be used | Can be used |
| Substitution | Yes | Yes, with user-based variations | Yes, with user-based variations |
| Encryption | Possible (if real-time access is not needed) | Less Ideal (performance overhead) | Less Ideal (performance overhead) |
| Nulling | Simple, but minimal protection | Can be used for limited masking | Can be used for limited masking |
| Noice addition | Can be used along with other technique | Can be used along with other technique | Can be used along with other technique |
Benefits of Dynamic Data Masking:
Dynamic Data Masking benefits an organization’s data security posture and compliance efforts in the following ways.
- Data Privacy Compliance: It plays a pivotal role in assisting organizations in complying with stringent data protection regulations, such as GDPR, PCI DSS, HIPAA, LGPD, and more.
- Customizable Security Policies: Dynamic Data Masking’s ability to enforce obfuscation rules and integrate with Role-Based Access Control (RBAC) allows organizations to tailor security policies according to user roles and needs.
- Preventing Data Breaches: It dynamically masks data by user permissions and limits the potential impact of unauthorized access, significantly reducing the risk of sensitive information falling into the wrong hands.
Use Cases of Dynamic Data Masking:
Dynamic Data Masking obfuscates sensitive information in real-time, providing an additional layer of security to prevent unauthorized access to sensitive information. Here are some common use cases of dynamic masking:
- Production Environments: Dynamic masking shines in live production databases, offering an extra layer of security without compromising the utility. This capability is particularly crucial in sectors where real-time access to sensitive information is imperative.
- Testing and Development: Production data is often necessary to test applications accurately in testing and development environments. However, exposing sensitive information to developers and testers can pose security risks. Dynamic masking allows organizations to use realistic information for testing while protecting sensitive information.
- Data Analytics and Reporting: Organizations often use data analytics and reporting tools to analyze large datasets and derive insights. Dynamic masking can help organizations anonymize sensitive information while allowing analysts to derive meaningful insights.
- Compliance Requirements: Many industries, such as healthcare (HIPAA), finance (PCI DSS), and government (GDPR), have strict regulations regarding the protection of sensitive data. Dynamic masking can help organizations comply with these regulations by ensuring that only authorized individuals can access sensitive information.
- Outsourcing and Offshoring: Companies that outsource or offshore specific business processes may need to share sensitive data with external partners. Dynamic masking ensures that sensitive information remains hidden from third-party vendors who do not need access to it.
- Role-Based Control: Dynamic masking can be integrated with role-based access control systems to ensure only users with the appropriate permissions can view sensitive information. This helps organizations enforce the principle of least privilege and minimize the risk of data breaches.
In conclusion, Dynamic data masking is a robust solution for safeguarding sensitive information in various environments. Its flexible features, including real-time obfuscation and role-based access control, offer organizations a versatile tool to ensure data security while facilitating efficient data utilization. It is a pivotal asset in today’s data-driven landscape, enabling organizations to conduct thorough analyses without compromising data integrity or regulatory compliance.
FAQ:
How does Dynamic Data Masking differ from static masking?
Dynamic Data Masking differs from static data masking by dynamically applying masking rules at runtime based on user queries or access privileges. In contrast, static data masking permanently alters data before storage, limiting its applicability in dynamic environments.
Can skilled attackers bypass Dynamic Data Masking?
While Dynamic Data Masking provides an additional layer of security, skilled attackers may attempt to bypass masking controls through advanced techniques such as SQL injection or privilege escalation. Continuous monitoring and proactive security measures are essential to detect and prevent such attempts.
Does Dynamic Data Masking support granular access control policies?
Yes, Dynamic Data Masking supports granular access control policies by enabling organizations to define masking rules based on user roles, privileges, or sensitivity levels. This ensures that only authorized users can access unmasked data while maintaining confidentiality and compliance.
Can Dynamic Data Masking be applied to unstructured data formats like documents or images?
Dynamic Or On-The-Fly obfuscation is a more versatile option and can handle both structured and unstructured data, offering greater flexibility for complex masking needs than Static Masking.





