Building Secure GenAI Ecosystem: The 10 Failure Modes Behind Most Incidents (Part 1)
Enterprise GenAI Security, Explained in Two Parts
As enterprises increasingly integrate large language models (LLMs) into core operations—from customer service chatbots to internal decision-making tools—the risks have evolved. A single prompt can steer behavior, retrieval can pull the wrong data, and an answer can become an action—meaning the boundary between “text” and “system behavior” is thinner than most security programs were built for. The OWASP Top 10 for LLM Applications provides a critical roadmap for identifying and mitigating these threats. For security teams and enterprise architects, understanding these risks is only half the battle; the real challenge lies in implementing effective security controls that directly address these vulnerabilities.
This guide provides a detailed framework for mapping enterprise security controls to the OWASP LLM Top 10, creating an actionable blueprint for securing your organization’s LLM implementations. This series is intentionally split into two blogs so readers can absorb the full story without losing the thread:
- Part 1: The “why” + LLM01–LLM05 + the control mapping approach
- Part 2: LLM06–LLM10 + The “how” at scale + lifecycle-managed governance + a 30/60/90 plan
Why both matter: Part 1 covers the most common early failure modes (inputs, leakage, supply chain, poisoning, unsafe outputs). Part 2 completes the picture by addressing agent/tool risks, vector retrieval weaknesses, misinformation, and unbounded consumption, and then shows how to operationalize controls at scale.
Summary
- Input filtering and least-privilege tool access form the primary defense-in-depth against prompt injection and can materially reduce risk, even though the class of vulnerability is unlikely to be fully eliminated.
- New entries, such as System Prompt Leakage, demonstrate why secrets should never reside in prompts; instead, enforce access controls outside the model (IAM/RBAC, DLP, retrieval ACLs) to ensure protection is consistent and auditable.
- Enterprise mapping aligns these risks with controls from frameworks such as NIST AI RMF and CIS Controls 8.0, enabling compliance while addressing LLM-specific vulnerabilities.
- Implementation challenges include striking a balance between innovation and security. Enterprises must balance GenAI innovation with security—moving fast without creating new paths for data leaks, unsafe automation, or uncontrolled access.
- A phased rollout with deliberate human oversight is the most practical path for enterprises: start narrow, validate controls in production, and expand permissions and automation only after monitoring and evaluation prove stable. NIST notes GenAI may require different levels of oversight and, in many cases, additional human review, tracking, documentation, and management oversight.
Why This Mapping Matters
A normal app usually has a clear perimeter: user → UI → API → database. An LLM app is different: it pulls context from documents, tickets, chats, wikis, and SaaS connectors; it can call tools; and it produces outputs that humans (and sometimes automation) act on. That combination creates a new class of security failures—failures that look less like “bugs” and more like untrusted language steering systems and data.
To keep this grounded, this blog uses the OWASP GenAI Security Project’s LLM Top 10 as a reference taxonomy—but the point here isn’t to repeat OWASP. The goal is to translate those risks into enterprise security controls your teams already understand: IAM, DLP, AppSec, SOC monitoring, vendor risk, SDLC gates, and cloud cost controls. An enterprise can use OWASP’s AI risk list to identify what could go wrong, and then use NIST AI RMF and CIS Controls to decide how to manage and reduce those risks.
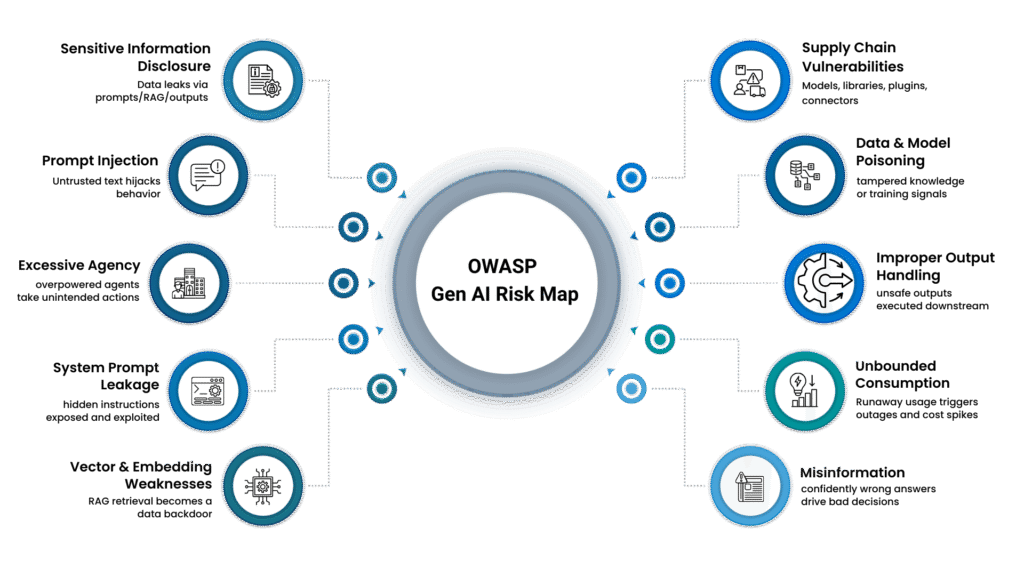
Understanding The 10 Failure Modes (LLM 01 → LLM 05)
The OWASP LLM Top 10 represents the most critical security risks facing applications that leverage large language models. Unlike traditional application security concerns, these vulnerabilities arise from the unique characteristics of LLMs: their training on vast datasets, their ability to generate content, and their integration into complex enterprise workflows.
LLM01: Prompt Injection (Prompt Hijacking )
Prompt injection occurs when attackers manipulate LLM inputs to override intended model behavior or system instructions, bypass safety controls, or extract sensitive information. This can happen through direct user input or indirectly through external content sources that the LLM processes. This tops the list due to its prevalence in real-world exploits and techniques like RAG and fine-tuning don’t fully mitigate it.
Enterprise Security Controls
Prevent
- Assume anything the user types (or any text pulled from documents) could be malicious. Treat it like you would treat text entered into a website form.
- Do not let the model directly use external systems. Add a strict approval layer that decides what actions are allowed (tool allowlists, scoped permissions).
- Only pull information that the user is allowed to see. If a document contains lines that look like “instructions,” remove or ignore those lines before sending the text to the model.
- Keep the “rules” separate from the “conversation.” Store the system rules in a secure location and separate them from user messages or document text.
Detect
- Keep safe records of what happened, including the user request, the document text used, any requested actions, and the final response (with sensitive data removed).
- Watch for suspicious behavior, such as repeated attempts, requests to export large amounts of data, requests to perform administrator-level tasks, or activity occurring at unusual times.
Respond
- Have an emergency switch to stop all actions immediately. The assistant can continue to answer questions, but it must stop performing any actions that modify systems or access additional data.
- If you suspect that data or access has been exposed, invalidate access immediately. Cancel the access keys or login tokens used to connect to other systems and issue new ones.
Note: Prompt injection can also be used to extract hidden instructions (“system prompt leakage”), which is why we address it explicitly later as its own failure mode (LLM07).
LLM02: Sensitive data leaks (Sensitive Information Disclosure)
LLMs may inadvertently expose sensitive data from their training sets, proprietary information from system prompts, or confidential data from user interactions. This risk is amplified when models are fine-tuned on enterprise data or when they have access to internal knowledge bases.
Enterprise Security Controls
Prevent
- Check user inputs and AI replies for private data; block, hide, warn, or require a reason.
- Mask/redact private details before sending text to the AI, not only after it replies (post-output redaction is a last line of defense).
- Store chats only as long as necessary, and restrict access to them.
- Don’t store passwords or access keys in prompts or memory; keep them in a secure storage location.
Detect
- Alert when private data appears in inputs or replies.
- Monitor for cross-user leakage signals (similar sensitive entities showing up across unrelated sessions).
Respond
- Delete or lock affected chat sessions where possible.
- Pause connections to email, files, tickets, and databases until reviewed.
- Handle it as a privacy/security incident and involve the right teams.
- Implement comprehensive data classification schemes before any LLM training or fine-tuning.
LLM03: “AI supply chain” compromise (Supply Chain Vulnerabilities)
Your GenAI system depends on pre-trained models, embeddings libraries, vector DB plugins, agents/tools, training data, deployment infrastructure, and data pipelines—often sourced from third parties. A compromised component can quietly reshape behavior or exfiltrate data.
Enterprise Security Controls
Prevent
- Maintain an AI-BOM: models, datasets, prompts/templates, tools, connectors, vector indexes.
- Vendor due diligence (security posture, provenance, licensing, data handling).
- Integrity controls: signed artifacts, pinned versions, controlled registries.
Detect
- Alert on “new model/tool/version” appearing outside approved pipelines.
- Continuous dependency and vulnerability scanning for AI stacks.
Respond
- Rollback plan (model + prompts + indexes), revoke compromised integrations, and rotate credentials.
LLM04: Poisoned training (Data and Model Poisoning)
Attackers inject malicious data into training sets or feedback loops, causing models to learn incorrect associations, embed backdoors, or degrade in performance for specific inputs.
Enterprise Security Controls
Prevent
- Provenance + approvals for ingestion sources (especially external).
- Quarantine and validate documents before indexing (malware scan + content checks).
- Do not let user feedback automatically become training data without review.
Detect
- Regression evaluations and drift detection (behavior shifts after corpus/model updates).
- Anomaly monitoring for ingestion spikes or unusual content patterns.
Respond
- Rollback to known-good model/corpus; purge poisoned docs; re-embed clean sources.
LLM05: Unsafe downstream execution (Improper Output Handling)
When LLM outputs are passed to downstream systems without proper validation, they can trigger injection attacks, execute malicious code, or cause unintended system behaviors. OWASP defines improper output handling as insufficient validation/sanitization of LLM outputs before passing them downstream, and also points out that it can lead to XSS/CSRF as well as SSRF, privilege escalation, or even remote code execution depending on the integration.
Enterprise Security Controls
Prevent
- Require structured outputs (schemas) + strict parsers.
- Make sure text is handled as plain text (data), not as code, based on where you’re using it (HTML/SQL/shell).
- Human approval for high-impact actions; “two-person rule” for irreversible ops.
Detect
- Flag outputs containing commands, secrets, suspicious URLs, or injection patterns.
- Monitor automation actions triggered by LLM outputs.
Respond
- Disable the automation path; audit changes; rotate secrets; patch validation gaps.
- Treat all LLM outputs as untrusted user input requiring validation.
- Run LLM-generated code in sandboxed environments with minimal permissions.
Bottom Line
So far, we have focused on the top five failure modes that typically surface first when GenAI moves from pilot to production: prompt injection, sensitive information disclosure, supply chain exposure, data/model poisoning, and improper output handling. The common thread is simple—LLM apps collapse traditional trust boundaries. Untrusted text can steer behavior, internal data can leak through retrieval and responses, third-party components can become silent exfil paths, poisoned knowledge can distort decisions, and “helpful” outputs can turn dangerous when downstream systems treat them as executable. The control mapping in this blog shows how to contain these risks using familiar enterprise guardrails: least privilege, DLP/redaction, vetted dependencies, ingestion validation, and strict output validation.
Part 2 completes the picture by covering what shows up as GenAI scales: excessive agency, system prompt leakage, vector/embedding weaknesses, misinformation, and unbounded consumption, followed by a practical operating model and a realistic 30/60/90 rollout plan. If Part 1 helps you secure the entry points, Part 2 helps you secure the scale points—agents, RAG, and production economics.
Read Part 2 to get the full blueprint and turn this into an end-to-end program.