Data Masking vs. Encryption: Which Shield Protects Against a $4.88M Breach?
Masking vs. Encryption: When, Why, and Where to Use?
Data security is a non-negotiable priority for organizations today, especially considering how frequent attacks get more sophisticated over time. In 2024, the average cost of a data breach rose to $4.88 million, marking a 10% increase from the previous year. Alarmingly, almost half (46%) of breaches involve customer PII data, highlighting the importance of having strong data protection measures in place. This blog delves into two essential methods for securing sensitive data: Masking and Encryption. Understanding their differences, use cases, and complementary roles is vital for strengthening data management practices and ensuring compliance with privacy regulations.
Understanding Data Masking: The Data Disguise Artist
Data masking replaces sensitive information with realistic but fictional equivalents, preserving format and usability while rendering original values irrecoverable. For instance, a credit card number “4415 1230 000 8675” is changed to “0301 9864 1640 3677” or “XXX XXXX XXXX 1234” using algorithm-generated values, retaining structure but eliminating exposure risks.
Unlike Encryption, which scrambles data, masking generates proxy data that mimics the original but contains no genuine information. This makes it invaluable for scenarios where data must be accessed but not exposed in its original form, such as in software development, testing, or analytics.
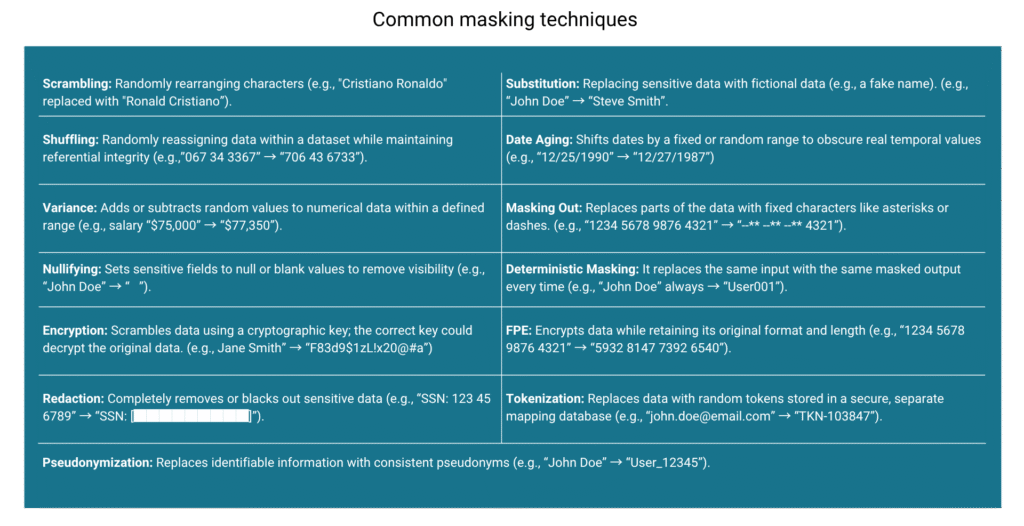
Masking Techniques and Types
Different use cases call for different masking techniques. Here are the most common:
- Static Masking: It creates a sanitized copy of the production database for non-production environments. Since the masked copy is stored permanently, much before the copy was requested, it is suitable for a long-term masked dataset for dev/test.
- Dynamic Masking: It is applied in real-time when a user accesses the data without changing the source, making it suitable for production environments. Here, the masked data is a temporary or runtime-only phenomenon.
- On-the-fly masking: Transforms data during transfer, bypassing staging delays in DevOps pipelines. Though similar to static masking, it is suitable for instant masking during provisioning.
- Referential Masking: Masks data consistently across related datasets to preserve relationships and integrity.
Understanding Data Encryption: The Digital Vault
Data encryption transforms plain text (readable data) into ciphertext (unreadable data) using cryptographic algorithms and a key. This ensures that even if the data is intercepted, it cannot be understood without the corresponding decryption key. Encryption is widely used for protecting sensitive data at rest (stored on devices) or in transit (sent over networks).
For instance, when you enter your credit card details on a secure website, the data is encrypted before being transmitted, ensuring it remains confidential during transfer. Unlike masking, encryption is reversible—authorized users with the key can restore original data.
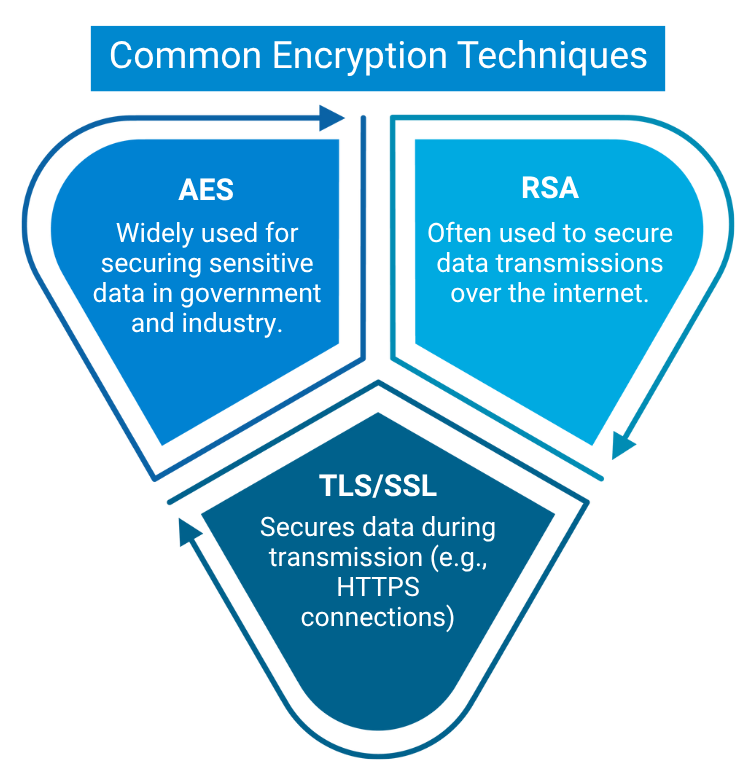
Encryption Techniques and Types
Encryption methods vary based on key management approaches and intended use cases:
- Symmetric Encryption: The same key is used for both encryption and decryption (e.g., AES-128 and AES-256). It offers speed and efficiency, but depends on how securely the encryption key is shared.
- Asymmetric Encryption: Uses a public key for encryption and a private key for decryption (e.g., RSA).
Encryption can be applied at various levels
- File-level encryption: Protects individual files or documents.
- Database encryption: Secures entire databases or specific columns.
- End-to-end encryption: Ensures data remains encrypted throughout its lifecycle, such as in enterprise content services or cloud data management.
- Data-at-rest encryption: Protects stored information in databases, file systems, and backup media, ensuring data remains secure even if storage devices are compromised.
- Data-in-transit encryption: Secures information moving between systems, applications, or networks, preventing interception during transmission.
- Application-level encryption: Occurs within software applications before data reaches databases, providing granular control over what information gets encrypted.
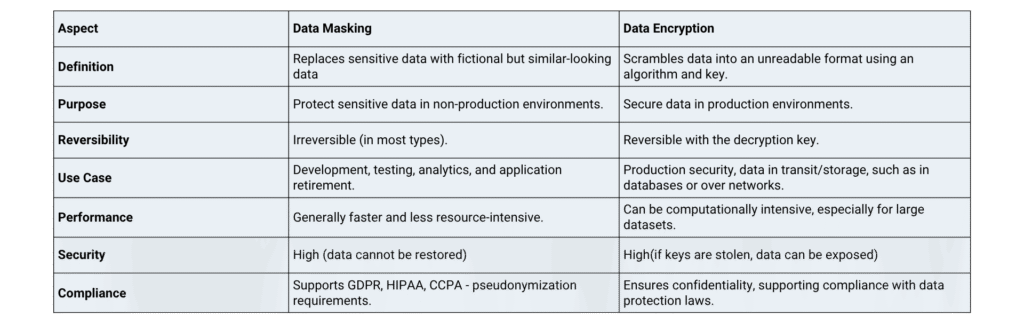
Key Differences: Data Masking vs. Encryption
To better understand when to use each method, let’s compare them side by side:
When and Why to Choose Masking or Encryption
Use Data Masking When:
- Sharing data with developers, testers, training, analytics, or third parties
- Building training or machine learning models
- Running analytics on data that doesn’t need real values
- Managing application retirement to preserve historical data in a non-sensitive format
Example: A software development team needs a realistic dataset for testing, but should not be given real customer data.
Use Data Encryption When:
- Transmitting sensitive information over networks
- Storing data in databases, file systems, or backups
- Ensuring secure access to production environments
- Protects unstructured data like files, images, or videos stored long-term
- Meeting regulatory requirements for data security
Example: Encrypting customer payment details stored in a database to protect them from unauthorized access (Encryption Consulting).
Complementary, Not Competitive: Where They Work Best
Data masking and encryption are not mutually exclusive. They address different aspects of data security and privacy compliance. A layered approach—combining both techniques—offers robust protection across the data lifecycle, from enterprise archiving to enterprise AI and beyond.
Ready to implement these strategies?
A smart combination of the two is essential for risk reduction, regulatory adherence, and long-term trust. Discover how Solix’s enterprise-grade data masking and encryption solutions help organizations like yours reduce breach risks, streamline compliance, and operationalize data security. Explore Solix’s approach to protecting sensitive data.
Learn more:
“How to Comply with Consumer Data Privacy Regulations?” This latest blog offers actionable steps to ensure compliance with consumer data privacy regulations and protect your business from costly violations. Read it now!