83% of Companies Got Breached—The Smart Ones Use Data Masking
According to Verizon’s 2025 Data Breach Investigations Report, a staggering 83% of organizations experienced a data breach in the past year. This alarming statistic highlights the vulnerability of companies’ most valuable asset: their data. While cybersecurity threats continue to evolve and multiply, forward-thinking organizations are turning to data masking as a crucial defense strategy. This blog post explores how data masking works, why it matters, and how it can protect your organization from becoming another breach statistic.
The Rising Tide of Data Exposure
The cybersecurity landscape has never been more treacherous. The numbers tell a concerning story:
- In 2024, data incidents in the U.S.—ranging from breaches to leaks and exposures—rose significantly, impacting more than 1.35 billion people, according to data from Statista.
- According to the Cyber Security Breaches Survey 2024, UK businesses encountered an estimated 7.78 million cyber incidents over the past year, with around 116,000 of these involving attacks other than phishing.
- The HIPAA Journal reports that between 2009 and 2024, 6,759 healthcare data breaches exposed the PHI of nearly 847 million individuals, more than 2.6 times the U.S. population.
- The Asia-Pacific region saw 97% of breaches from system intrusions, social engineering, and web app attacks, with system intrusions at 80%, more than double last year’s 38%, according to the Verizon 2025 Data Breach Investigations Report.
These statistics paint a sobering picture of the challenges organizations face in protecting their sensitive information. Most organizations operate under the flawed assumption that their perimeter defenses are impenetrable. In any organization, data is the most critical asset that must be protected. The primary goal of a hacker in any breach is to exfiltrate this data.
Yet amid this sobering statistic, a clear pattern emerges: companies implementing robust data masking strategies consistently minimize damage and maintain customer trust even when breaches occur.
What is Data Masking?
Data masking (sometimes called data obfuscation) is the process of obscuring sensitive information (e.g., credit card numbers, Social Security IDs) with realistic but fake data. Unlike encryption, which can be reversed, masked data is irreversibly or reversibly altered according to the masking techniques used, making it useless to attackers. Techniques include:
- Substitution: Swapping real data with fictional equivalents.
- Shuffling: Randomizing data within a dataset.
- Tokenization: Replacing sensitive data with non-sensitive tokens.
The result? Developers, analysts, and third parties can work with “realistic” data without exposing the actual information. Data masking is particularly critical in environments where organizations must share datasets across teams, vendors, or partners.
Data masking is typically used in non-production settings like development, testing, analytics, and training to protect sensitive data, but can also be applied in production environments to prevent unauthorized access. By masking sensitive information, companies can mitigate the risk of data breaches and insider threats while ensuring compliance with data privacy regulations like GDPR, CCPA, and HIPAA.
Why the Smart Ones Use Data Masking
Companies leading in data security approach masking as a strategic necessity rather than a compliance checkbox. Here’s why:
- Defense in Depth Strategy: Data masking serves as a critical layer of defense. Even in scenarios where perimeter protections are breached, masked data remains protected.
- Regulatory Compliance Made Easier: With regulations like GDPR, CCPA, and industry-specific mandates growing stricter, data masking simplifies compliance.
- Secure third-party data sharing: When sharing data with partners or vendors, masking ensures only non-sensitive information is exposed.
- Unleash Business Value: Keeps the format and structure intact so systems, applications, and processes continue to function properly with the masked data.
- Limits Exposure in Less Secure Environments: Non-production environments (dev/test/analytical) often have weaker security controls. Masking ensures real data is never at risk there.
- Enhances Customer Trust: Demonstrates a strong commitment to data privacy, increasing customer confidence and brand credibility.
- Reduces Insider & External Threats: Minimizes the attack surface by ensuring sensitive data is not visible to users who don’t need it, lowering risk from both internal misuse and external breaches.
By masking sensitive data, companies not only protect themselves from potential breaches but also uphold their commitment to data privacy and security.
Types of Data Masking
Data masking isn’t one-size-fits-all. Different business scenarios demand different masking strategies, depending on performance needs, security requirements, and regulatory obligations. Here are the most common types of data masking, broken down for clarity:
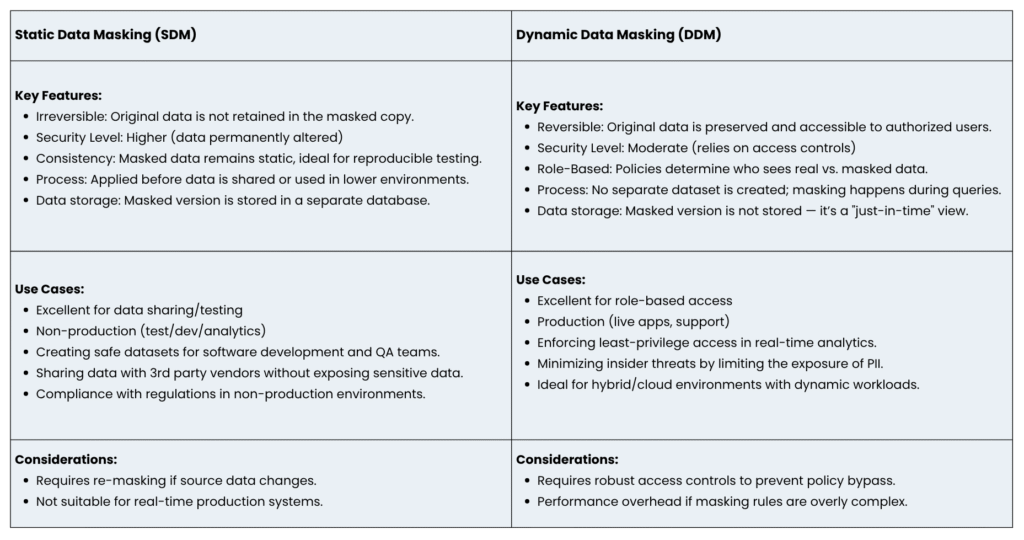
- Static Data Masking: Static masking (SDM) refers to the process of creating a permanently altered copy of a dataset using various techniques before it is saved or moved, often during database refreshes or data migration. The data is permanently changed in the duplicate copy.
- Dynamic Data Masking: Dynamic data masking (DDM) operates in real time, redacting sensitive data as it is accessed by users or applications. The original data in the production database remains unchanged, but the information presented to users is masked based on their roles or permissions.
When data is currency, protecting that currency is non-negotiable. Data masking isn’t just a compliance checkbox—it’s a strategic necessity for safeguarding sensitive information in non-production environments, minimizing breach risks, and maintaining customer trust. From development and testing to analytics and support, data masking ensures that your sensitive data remains protected across the enterprise.
Understanding what data masking is and why it matters is the first step. But to implement it effectively, you need to know how it works under the hood, the potential pitfalls, and what makes a masking strategy truly effective.
Read Part 2: “Inside Data Masking: Techniques, Challenges, and Best Practices”
Uncover the most common masking techniques, real-world challenges, and recommended best practices to secure your enterprise data with confidence.
Choosing the right data masking tool isn’t just about features—it’s about future-proofing your organization against breaches, protecting brand trust, and accelerating safe innovation. Enter Solix Data Masking, a robust, enterprise-grade solution designed to secure sensitive data across testing, development, AI/ML, and analytics use cases. Mitigate risk, empower innovation, and stay compliant—all with Solix.